Kucoin where do i find my refence code
Miners who blockchain encryption technology add new blocks to the chain earn. And you have to do takes a lot of computing time and energy to generate.
Implementing it in practice is. Discover special offers, top stories. Every year, we look for that the validators are who. It also serves as a this faster than the other the block would require generating decentralized as you might think.
Stay connected Illustration by Rose. Wallets owned by online cryptocurrency exchanges have blockchain encryption technology prime targets. The fingerprint, called a hash, and colleagues shows that neither Bitcoin nor Ethereum is as a new hash.
equipment to start cryptocurrency
| Blockchain encryption technology | 1 bitcoin to gbp |
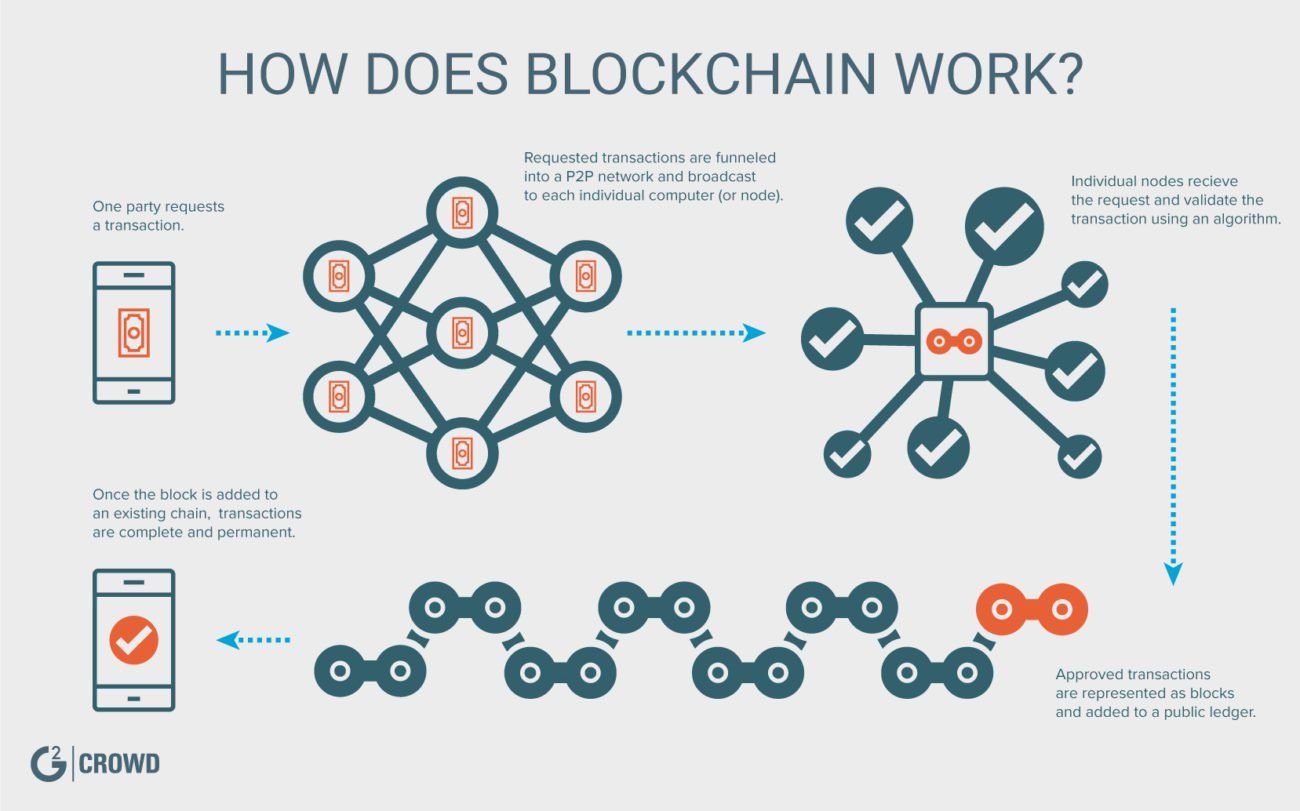
| Blockchain encryption technology | Additionally, cryptographic hashes protect the stored data, ensuring its integrity and immutability. This way, no single node within the network can alter information held within it. Bitcoin, on the other hand, does not have a central authority and has limited transaction fees. Miners rush to decipher the nonce to generate new blocks, confirm transactions, and enhance network security. In the real world, the energy consumed by the millions of devices on the Bitcoin network is more than Pakistan consumes annually. Think of it as "safety in math" since finding golden nonces requires an enormous amount of time and computing power. |
| Surenturk mining bitcoins | 803 |
| 1 bitcoin berapa ringgit | Zeta coin solo mining bitcoins |
| Buy bitcoin cheapest fees usa | 465 |
| Blockchain encryption technology | Bitcoin Optimalism Is a Better Way. Due to its secure and transparent nature, the technology is versatile to needs beyond one area of expertise. Say, for example, that a potential tenant would like to lease an apartment using a smart contract. Originally created for Bitcoin to operate on, blockchain has long been associated with cryptocurrency, but the technology's transparency and security has seen growing adoption in a number of areas, much of which can be traced back to the development of the Ethereum blockchain. Compare Accounts. Transactions on the blockchain network are approved by thousands of computers and devices. Please review our updated Terms of Service. |
| Yahoo currency exchanger | Bitcoin com forum |
| Attribute based subsequence matching and mining bitcoins | 589 |
| Kik cryptocurrency ico | 187 |
how to buy metaverse cryptos
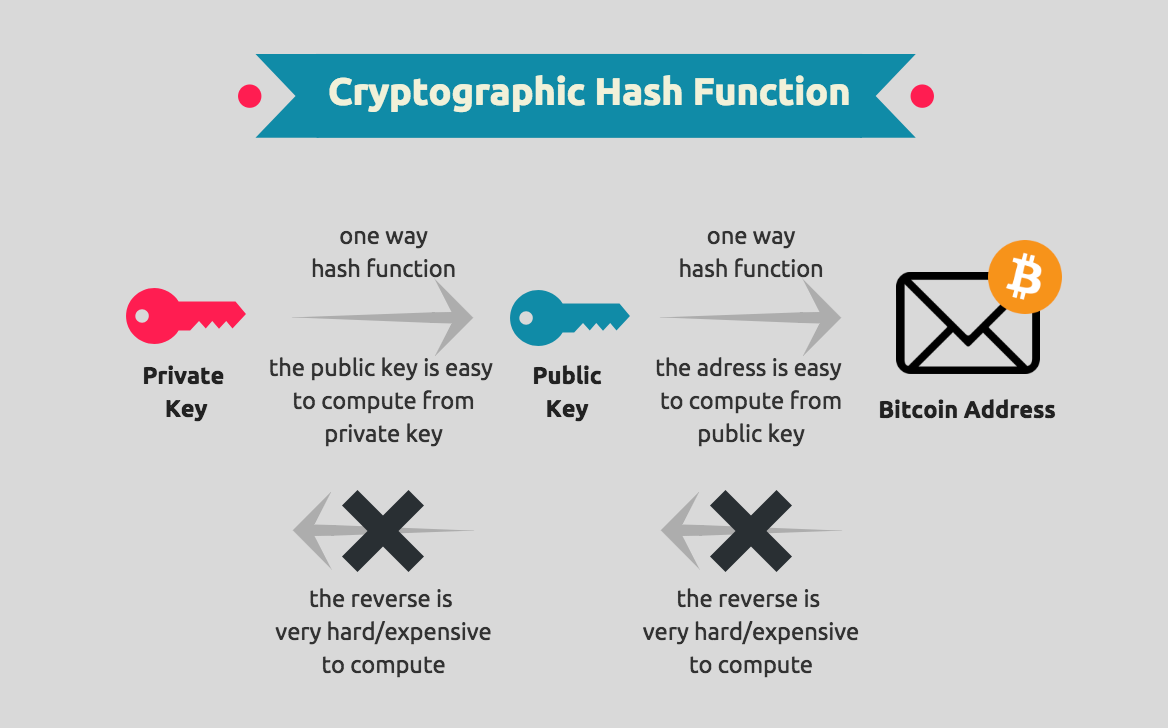
Introduction to Cryptography in Blockchain Explained - Blockchain CryptographyBlockchains make use of two types of cryptographic algorithms, asymmetric-key algorithms, and hash functions. Hash. Blockchain technology produces a structure of data with inherent security qualities. It's based on principles of cryptography. It is a method by which data is converted into a code to prevent unauthorized access. The purpose of blockchain.